2 Easy Ways to Protect Your Business from Cyber Attacks

Cyber-attacks are a continuous risk for all kind of businesses, and these attacks can be particularly damaging for telecom companies, because their network infrastructure is at the very core of their business. If the network faces a malicious attack, users may lose connectivity.
We all know that telecom security is going under many IT threats and different compliance requirements. Telecom companies have millions of customers, which is attraction for hackers and malicious attacks.
Arbor Network’s latest Annual Worldwide Infrastructure Security Report revealed that service providers are facing a numerous threats, including increasingly severe distributed denial of service (DDoS) attacks.
At following, there are two types of security products which are essentials for any business to secure their IT/telecom infrastructure.
- Web Application Firewall
- Telecom Attack Discovery
Web Application Firewall

Internet Banking, Corporate Mobile Apps, and Web based applications always face security threads and attacks. There are many types of attacks on web servers include SQL injection attacks, cross-site scripting (XSS) attacks, and DDoS attacks. Companies always wanted to know how they can you defend against these attacks.
Here are two ways which can help:
- Developing applications to prevent attacks
- Securing apps using specifically designed web application firewalls like PT Application Firewall
A web application firewall (WAF) is an online security solution that filters out bad HTTP traffic between a client and web application. Web Application Firewall is an essential product for all online running businesses like Internet Banking, Corporate Mobile Apps, and Web based applications.
Telecom Attack Discovery
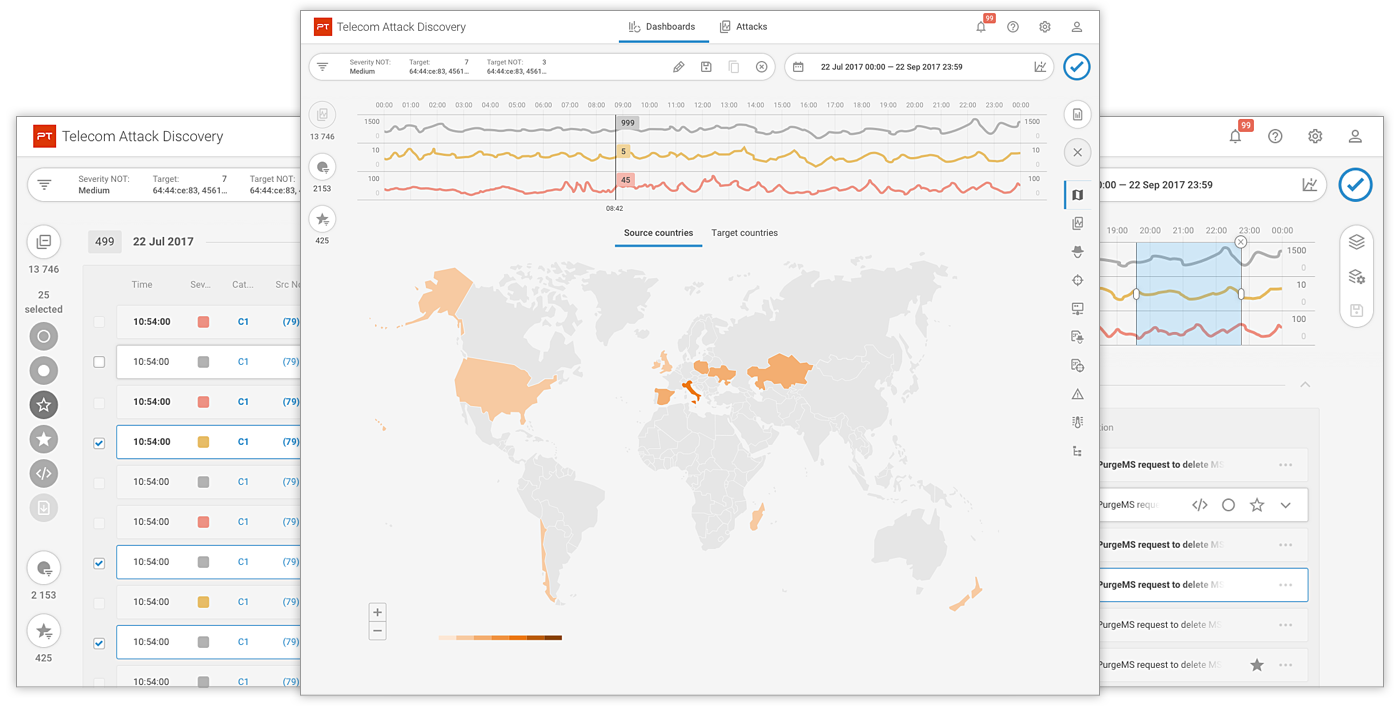
Telecom security is rapidly becoming a cause for concern of many businesses. To establish strong relationship with millions of customers subscribing to services ranging from cable, the Internet, home and mobile phone service and even data centers, the telecom industry is working in an environment that needs proven cyber security and information assurance.
PT Telecom Attack Discovery researchers know exactly how to find out all types of malicious activity, including:
- Call and SMS interception
- Subscriber location tracking
- Fraud, including manipulation of USSD codes to transfer money and billing system manipulation to make free calls
- DoS targeting a subscriber or network segment
- Sensitive data leakage
Click here to learn more about PT telecom attack discovery.